Penetration Testing 101
If you've ever wondered what it's like to step into the shoes of a hacker—but the ethical kind—this post is your starting point.
What is Pen Testing and Why Should You Learn It?
Hey there, fellow tech enthusiasts! 👋 If you’ve ever wondered what it’s like to step into the shoes of a hacker—but the ethical kind—this post is your starting point. I’m kicking off a blog series that’ll take you deep into the world of pen testing (short for penetration testing), a must-know skill for anyone interested in cybersecurity or ethical hacking. Whether you’re a complete newbie or a tech-savvy pro looking to level up, this series will break down every stage of pen testing, from the first recon to the juicy exploits. Let’s dive in!
What is Pen Testing?
Penetration testing is like staging a mock heist on a digital vault. It’s a controlled, simulated cyber attack where ethical hackers use the same tricks as the bad guys to uncover vulnerabilities in computer systems, networks, or web applications—before the real threats get there. The goal? Find the weak spots, exploit them (safely and legally), and then help patch them up.
But it’s not just about breaking in. Pen testing is a structured process that reveals how secure (or insecure) a system really is. It’s like hiring a locksmith to test your doors—not to rob you, but to make sure no one else can. And it’s not just for big corporations or spy agencies. Small businesses, like an online shop protecting customer credit card info, or even developers writing apps, can use pen testing to stay safe.
Real-world scenario: A small e-commerce site gets hit with a data breach because of a weak login page. A pen tester could’ve spotted that flaw ahead of time, saving the business from a PR nightmare (and a hefty fine). Or picture a developer who learns pen testing and catches a bug in their code that could’ve let hackers slip in. That’s the power of this skill!
Why Should You Learn Pen Testing?
In today’s world, where cyber attacks are spiking—2024 saw a 30% jump in breaches according to IBM—pen testing isn’t just cool; it’s essential. Here’s why you should jump on board:
- Outsmart the Hackers: Learn how attackers think and strike, so you can lock down your systems—or your clients’—before they do.
- Career Goldmine: Cybersecurity jobs are booming, with pen testers in high demand. The U.S. Bureau of Labor Statistics predicts a 32% growth in info security roles by 2032. This could be your ticket to a gig as an ethical hacker or security analyst!
- Problem-Solving Thrills: Pen testing is like solving a high-stakes puzzle. Every system is a challenge, and every exploit is a win.
- Protect What’s Yours: Whether it’s your personal projects, your startup’s app, or a company’s network, knowing pen testing means you can defend it.
Plus, there’s an undeniable rush in legally cracking into systems and finding hidden flaws. It’s part detective work, part adrenaline—perfect for anyone who loves a challenge.
Tools of the Trade
Before we dive deeper, let’s look at some essential tools you’ll encounter in your pen testing journey:
1
2
3
4
5
6
7
8
9
10
11
# Basic network reconnaissance with Nmap
nmap -sV -p 1-1000 target.example.com
# Finding subdomains with Sublist3r
python sublist3r.py -d example.com
# Vulnerability scanning with Nikto
nikto -h https://target.example.com
# Password cracking with Hydra
hydra -l admin -P wordlist.txt target.example.com http-post-form "/login:username=^USER^&password=^PASS^:F=Login failed"
A Sneak Peek Into the Series
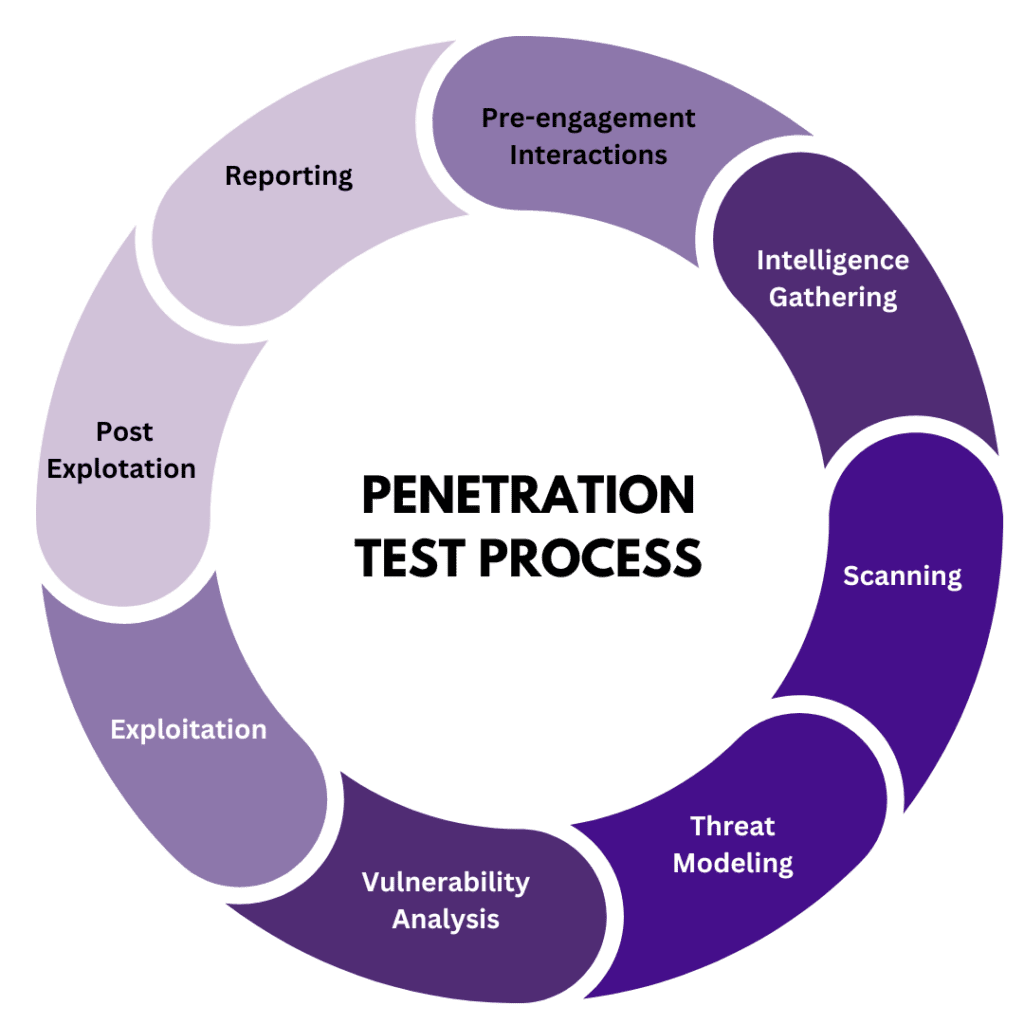
This isn’t just a “read and nod” blog. We’re going hands-on through every stage of pen testing, inspired by the eJPT (eLearnSecurity Junior Penetration Tester) course—a top-notch certification that covers the full hacking lifecycle. Here’s what’s coming:
1. Planning and Scoping
We’ll start by setting the stage—defining goals, boundaries, and rules. Think of it as drawing the map before the mission.
1
2
3
4
5
6
7
8
9
10
# Example scope definition in Python
def define_scope():
scope = {
"target_systems": ["192.168.1.0/24", "web.example.com"],
"excluded_systems": ["192.168.1.5", "admin.example.com"],
"testing_window": "2025-05-15 22:00 to 2025-05-16 05:00",
"allowed_techniques": ["port scanning", "vulnerability assessment", "exploitation"],
"prohibited_techniques": ["DDoS", "social engineering", "physical access"]
}
return scope
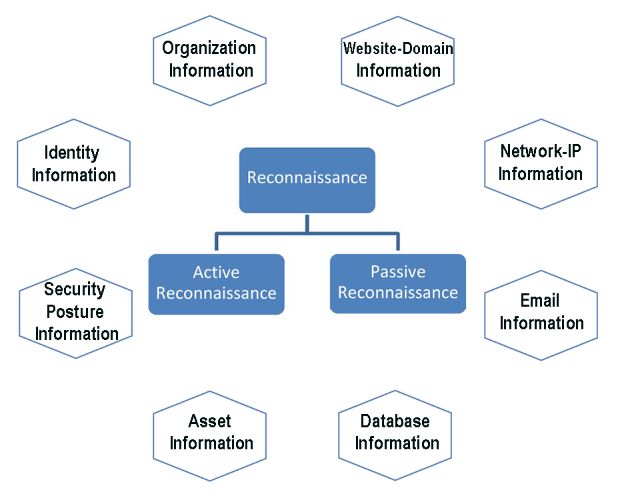
2. Reconnaissance (Host Discovery)
Next, we’ll play detective, gathering intel on our target—IP addresses, domains, and more—using tools like Nmap and Shodan. It’s all about knowing what you’re up against.
3. Scanning
Time to probe deeper. We’ll scan for open ports, services, and vulnerabilities, spotting the cracks in the system’s defenses.
1
2
# Advanced Nmap scan for service detection and OS fingerprinting
nmap -sS -sV -sC -O -p- --script vuln target.example.com -oA comprehensive_scan
4. Exploitation
Here’s where it gets fun—exploiting those weaknesses to break in. We’ll try real techniques, like cracking weak passwords or bypassing bad configs.
1
2
3
4
5
# Simple SQL injection example (for educational purposes only)
vulnerable_url = "http://example.com/page.php?id=1' OR '1'='1"
response = requests.get(vulnerable_url)
if "database error" not in response.text.lower():
print("Potential SQL injection vulnerability found!")
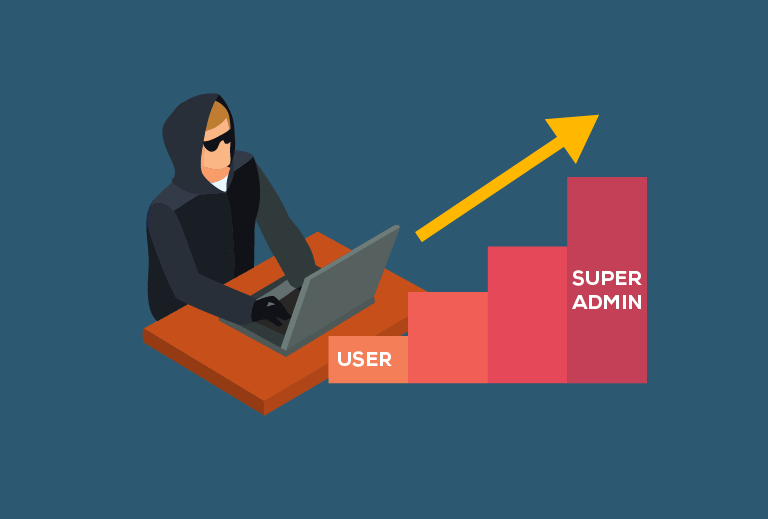
5. Post-Exploitation (Privilege Escalation & Persistence)
Once inside, we’ll dig into the juicy stuff: escalating privileges to gain more control and maintaining persistence to stick around undetected. Think of it as planting a flag and holding the fort.
6. Reporting
Finally, we’ll wrap up with pro-level reports—detailing what we found, how we got in, and how to fix it. This is what turns a hack into a solution.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Example Vulnerability Report Template
## Executive Summary
Brief overview of findings and risk assessment
## Vulnerability Details
### Critical Vulnerability: SQL Injection in Login Form
- **CVSS Score:** 9.8 (Critical)
- **Affected Component:** /login.php
- **Description:** The login form is vulnerable to SQL injection attacks...
- **Proof of Concept:** `' OR 1=1 --`
- **Remediation:** Implement prepared statements and input validation
## Remediation Timeline
- Critical issues: 7 days
- High issues: 14 days
- Medium issues: 30 days
Each post will pack practical examples and exercises you can try (safely, of course). For instance, during reconnaissance, you might use Nmap to map a test network. Later, we’ll tackle privilege escalation with tricks attackers use to climb the access ladder. It’s all building toward you becoming a confident ethical hacker.
Stay tuned for the next post, where we’ll kick off with Planning and Scoping. See you there!